Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Security holiday calendar - Part 1
As it was well received last year, we decided to do another security-focused holiday calendar this year. The concept was roughly the same, but instead of only adding security hardening modules, we’ve also added in some other security advice and blog posts to improve the variety. Now that we’re halfway through to 24 (or 25), let’s recap the first half of the calendar.
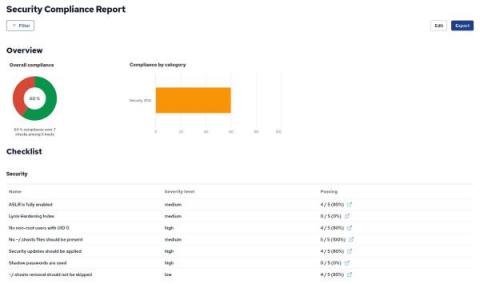
Building a Compliance Report based on inventory modules
In CFEngine Enterprise we collect information from each system in the infrastructure as inventory. Some inventory is available by default, and more can be added using modules or writing policy. You can use inventory information to create a Compliance Report with checks that determine if the information complies with your security requirements. In this blog post, we will use some modules from CFEngine Build which provide inventory data, and build a Compliance Report on top of those.
Top 5 benefits of network backup software
Grafana 9.3 feature: Grafana OAuth token improvements
As part of our efforts to improve the security of Grafana, we introduced a long-awaited feature in the latest Grafana 9.3 release that enhances Grafana’s OAuth 2.0 compatibility. The new Grafana OAuth token improvements, which are available in Grafana OSS, Grafana Cloud, and Grafana Enterprise, ensure that the user is not only logged into Grafana, but they’re also authorized by the OAuth identity provider.
The What, Why and How of Auto-Remediation in Cybersecurity
When you’re facing a cyberattack, waiting even just minutes to respond could be the difference between business as usual and a calamity. It may only take that long for threat actors to exfiltrate sensitive data or disrupt critical systems. That’s one reason why automating remediation is an essential ingredient in an effective cybersecurity strategy.
Cyber Attacks Are Getting Smarter... Are You Ready?
It feels like everything is getting a “smart” upgrade these days. From the cars we drive to how we operate our domestic appliances, almost every gadget has had a smart upgrade or now uses Artificial Intelligence (AI) to improve our lives – or so they claim…
How to Augment an Existing Data Lake with Exabeam and Cribl Stream
Organizations have different data lakes they use to search, whether it is Splunk, Qradar, or Sumo Logic just to name a few. Exabeam (UEBA Advanced Analytics) sits on top of those existing data lakes and pulls specific sources by running continuous queries every few minutes into Exabeam. The image below shows a Splunk query to pull windows event logs into Exabeam Advanced Analytics over the port (8089). The query is complex.
Graylog 5.0 - A New Day for IT & SecOps
We are excited to announce the release of Graylog 5.0! Graylog 5.0 brings updates across our entire product line, including changes to infrastructure, Security, Operations, and our Open offerings. For more detailed information on what’s changed, visit our changelog pages for Graylog Open and Graylog Operations/Graylog Security.
Torq Users Hit 1,000,000+ Daily Security Automations
Security automation is an increasingly critical element in optimizing enterprise cybersecurity postures. Today, Torq announced its users are executing more than 1,000,000 daily security automations using our security automation platform – a major milestone that underlines the traction and importance of unifying today’s complex security stacks.