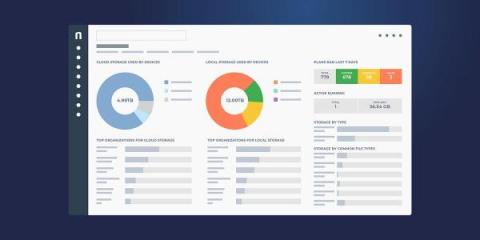
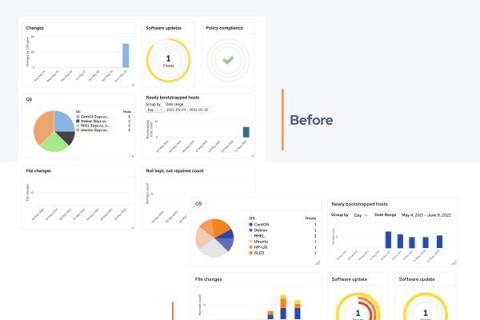
Exploring Ninja Data Protection
With image backup now generally available to our partners, Ninja Data Protection is ready for prime time. When we first launched Ninja Data Protection in 2020, our backup solution was a Windows-only, cloud-only file and folder backup solution. With several hundred partners adopting the solution and providing feedback, we were able to rapidly adapt our backup roadmap to customize the solution to our partners needs and wants.