Operation panopticon: How a weak IAM strategy led to the security camera hack across organizations
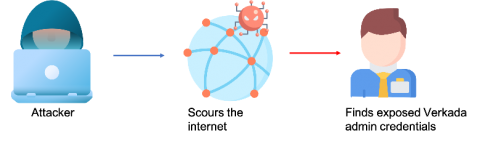
On March 9, 2021, Verkada, a software company that specializes in making security cameras for monitoring physical access control, was subject to a security hack. Hackers gained access to the video feed of at least 15 thousand cameras deployed across various locations and exposed the inner workings of hospitals, clinics, and mental health institutions; banks; police departments; prisons; schools; and companies like Tesla and Cloudflare.