Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
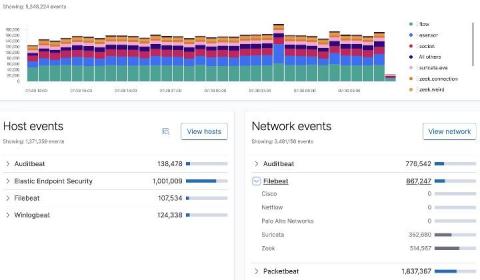
Collecting and analyzing Zeek data with Elastic Security
In this blog, I will walk you through the process of configuring both Filebeat and Zeek (formerly known as Bro), which will enable you to perform analytics on Zeek data using Elastic Security. The default configuration for Filebeat and its modules work for many environments; however, you may find a need to customize settings specific to your environment.
Fitness Websites Under Attack by Magecart
Our sources state that there has been a 20% increase in web-skimming attacks since the outbreak of the COVID-19 virus. Recently, we have witnessed some high-profile Magecart attacks on websites which have gained popularity during the pandemic, including fitness-based websites. The latest fitness-based website attack reported is YogaFit, who were compromised for over 6 weeks.
Data Loss Prevention and Security Basics You Need to Know
Cyberattacks are the “buzz word” that you hear when a company’s data has been breached. Sometimes the breach results in data being released on the internet. Other times, the hacker holds the data ransom in exchange for a large monetary payout. Data loss prevention and protection should be at the top of your list. Your data, after all, should be considered one of your most valuable business assets.
How to build a security team without becoming the enemy
Unsurprisingly, a lot of people say they don’t like working with security teams. Security teams often have ridiculous requirements, and it can be painful for everyone when releases get delayed. I’ve been guilty of thinking the same thing, so when I was approached at my job at Doximity to build a security team (without prior experience doing so), I knew I wanted to take a different approach.
Monitoring and Securing Cloud-Based Databases Is the Developer's Responsibility
Ivanti Integrates Ivanti Neurons Platform with Splunk Security Operations Suite
We have unveiled several exciting announcements recently, from the launch of Ivanti Neurons to all of our strategic partnerships and integrations (see the details on Intel and Qualys). In fact, we have had so much content to announce that we've needed to create a whole new blog category! But this train is not slowing down any time soon.
Data Security and Privacy at Home
Kubernetes Security Best Practices You Must Know
Kubernetes (k8s) enables you to efficiently orchestrate container management, in the cloud or on-premises. As a whole, k8s provides many benefits, including features for self-healing, automated rollouts and rollbacks, load distribution, and scalability. However, k8s is a highly complex platform and requires extensive configuration.
Enable TLS with Let's Encrypt and the HAProxy Kubernetes Ingress Controller
The HAProxy Kubernetes Ingress Controller integrates with cert-manager to provide Let’s Encrypt TLS certificates. When it comes to TLS in Kubernetes, the first thing to appreciate when you use the HAProxy Ingress Controller is that all traffic for all services travelling to your Kubernetes cluster passes through HAProxy. Requests are then routed towards the appropriate backend services depending on metadata in the request, such as the Host header.