Operations | Monitoring | ITSM | DevOps | Cloud
Networks
The latest News and Information on IT Networks and related technologies.
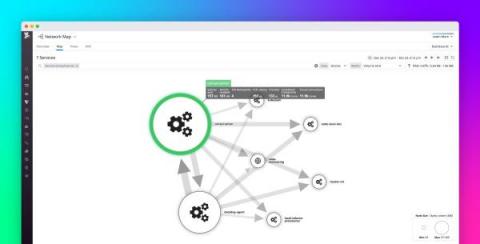
Datadog NPM now supports Consul networking
Consul is a service networking platform from HashiCorp that helps you manage and secure communication between microservices. You can use Consul with Kubernetes, and it supports on-prem, hybrid, and multi-cloud architectures. Consul service mesh provides a control plane which allows you to automate the management of traffic between your services via features like service discovery, DNS, load balancing, and routing.
Is Your Zero-Trust Solution Missing Half Your Network?
With hybrid work environments on the rise, enterprise networks are dealing with multiple remote connections, increasing the risk of breaches and other attacks. One way to mitigate these risks is by implementing Zero Trust Architecture (ZTA) into the enterprise network. Unfortunately however this does not address the full set of threats to the enterprise, as many of the zero-trust service providers and on-premises network solutions do not address the voice network.
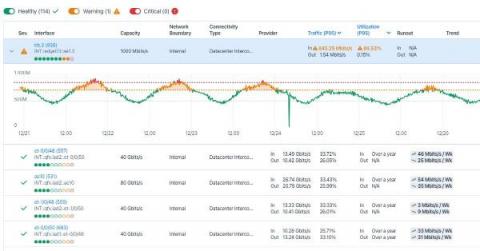
Network capacity planning made easy in 2022
Didn’t quite get to that task of capacity planning in December? Well, not to worry, this month Kentik has overhauled our Capacity Planning workflow and is introducing a slew of new features to make capacity planning easier and more intuitive than ever before. Those who are familiar with Kentik will know that one of our core offerings is the ability to monitor and plan actual network and interface utilization.
The Top 5 Use Cases for AIOps Today
By now, you’ve likely heard of AIOps, a technique that promises to inject new levels of efficiency into IT operations with the help of AI and machine learning. But what, exactly, does AIOps mean in practice? Which specific use cases can IT organizations enable or improve with the help of AIOps? Those may be more difficult questions to answer if you have yet to see AIOps at work in your organization.
How to use OpManager as an effective disk space monitor for your network monitoring environment
Disk space availability in servers is crucial. Applications that run on these servers save log files and write data to a database that is also installed on the server; if there isn’t enough disc space, the application may not work properly and may crash. Monitoring disc space is critical for IT administrators to maintain server performance and network availability by preventing a sudden and unexpected lack of server disc space.
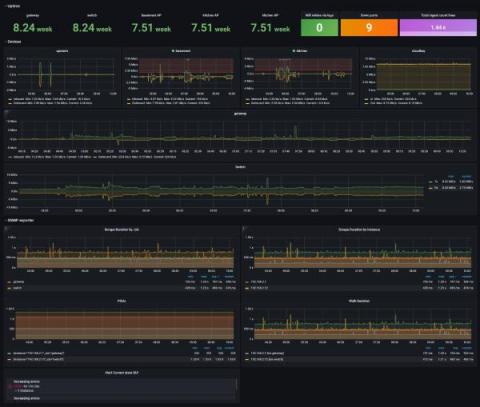
A beginner's guide to network monitoring with Grafana and Prometheus
Networks are the backbone of inter-communications within computer systems and applications. When networks go down or experience any interruption of service, the impact is widely felt and can result in significant service disruptions and lost revenue. This is why network monitoring is mission critical for organizations. Visibility into network performance is key to ensuring that network engineering teams can be more proactive and identify problems before those issues cause outages.
Why you need network monitoring?
Network monitoring is a continious analysis of a network to detect and correct any performance issues. Network monitoring involves collecting network statistics to determine the quality of services offered by the network. With tools like Icinga, it’s possible to monitor hardware and software in your network. Espacially in the pandemic when many employees work from home, it’s good to have a tool which checks the network permanently.