Operations | Monitoring | ITSM | DevOps | Cloud
%term
D2iQ: A Smarter Approach to Day 2 Operations
Implementing AIOps - Revolution Or Evolution
The underlying infrastructures behind IT systems have become complex and overloaded. A single incident in today’s IT stack can shut down large chunks of a business and cost it millions – or even billions. Because of that, many businesses consider implementing AIOps in their IT operations an important part of their future.
Top 15 Website Change Monitoring Tools
Life is full of surprises and we look at in a positive way. But the same cannot be said about business. In business, surprises are unwelcome and you have to be alert about changes happening around that will affect it. This helps in adapting to the new business landscape and change the way of doing business.
A Practical Approach to Incident Management Escalation
Incident escalation is one of those seemingly mundane issues, the importance of which is often underestimated. Simply put, the escalation process is used to flag issues so that the relevant personnel can respond to situations. Implementation of a well-designed escalation process, however, is anything but simple.
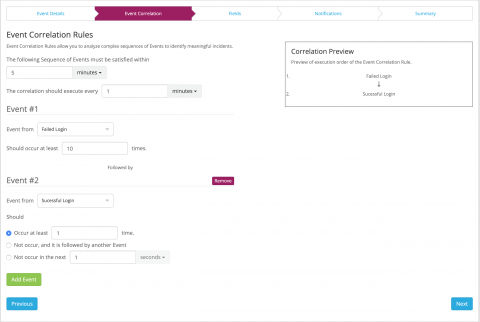
Announcing Graylog 3.1 RC 1
Today we are releasing the first Release Candidate of Graylog v3.1. This release brings a whole new alerting and event system that provides more flexible alert conditions and event correlation based on the new search APIs that also power the views. In addition, some extended search capabilities introduced in Graylog Enterprise v3.0 are now available in the open source edition in preparation for unifying the various search features.
Leading Chief Data Scientists Weigh in on Building Time Series Anomaly Detection
In our recent webinar on what it takes to build time series anomaly detection, industry experts Arun Kejariwal, Ira Cohen and Ben Lorica shared valuable advice for ways to successfully implement and execute anomaly detection systems in today’s increasingly complex corporate world.
Glitch List: July 2019
There’s never a dull moment in the world of anomaly detection. These are the glitches that the world’s largest organizations battled in the month of July.
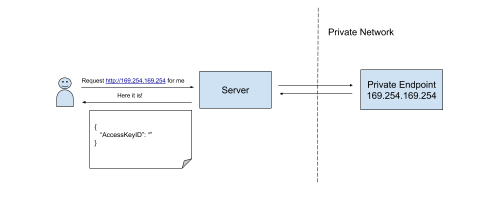
A Technical Analysis of the Capital One Hack
The recent disclosure of yet another cloud security misconfiguration leading to the loss of sensitive personal information made the headlines this past week. This particular incident came with a bit more information from the indictment of the accused party, allowing us to piece together the revealed data and take an educated guess as to what may have transpired leading up to the loss of over 100 million credit card applications and 100 thousand social security numbers.
Five worthy reads: Threat intelligence-the key to proactive cybersecurity
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore how cyber threat intelligence can aid organizations. Enterprises often end up spending a great deal of money on monitoring and wiring their perimeter with defensive security solutions. But is merely incorporating security solutions like firewalls, antivirus software, intrusion detection systems, web filtering, and encryption enough?