Operations | Monitoring | ITSM | DevOps | Cloud
%term
Meeting PCI DSS Network Security Requirements in Kubernetes Environments
How To Extend Firewalls to Kubernetes to Stop Breaking Existing Security Architectures
Why Can't We Be Friends? - Kubernetes in a Zone-Based Architecture World
Five worthy reads: Is your enterprise dealing with data sprawl properly?
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we define what data sprawl is and how organizations can cope with it effectively. Data sprawl—defined as the proliferation of data into endpoints, servers, applications, BYODs, operating systems, network environments, and even other geo-servers—can be a challenge to monitor and control.
Monitoring Apdex with Scout APM
There is no doubt that looking at response times and memory usage is essential to understanding the general health and performance of your application. But as I am sure you are aware, there is more than one way to monitor an application. Approaching monitoring from a different angle can be a powerful way of gaining new insights. If all you did was watch for high response times or areas of memory bloat, then you might overlook something far more simple: the user’s general level of satisfaction.
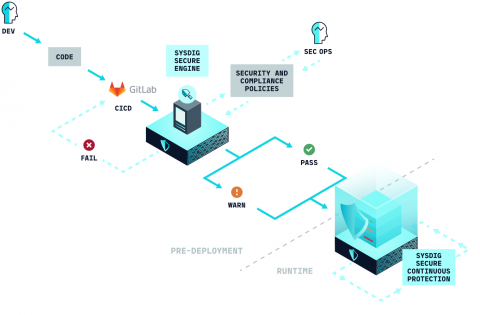
Integrating Gitlab CI/CD with Sysdig Secure
In this blog post we are going to cover how to perform Docker image scanning on the Gitlab CI/CD platform using Sysdig Secure. Container images that don’t meet the security policies that you define within Sysdig Secure will be stopped, breaking the build pipeline before being pushed to your production Docker registry.
AlertBot Tutorial: Setting up a TrueBrowser Page Monitor
AlertBot Tutorial: How To Run and View Test Log Reports
Why Context is Critical in a Data-Driven World
Research firm IDC predicts that overall data volumes will grow from 33 zettabytes in 2018 to 175 zettabytes by 2025. 50% of the data will come from IoT devices and nearly 30% of the data will get consumed in real-time by 2025. The data economy has changed the game on how enterprises will need to work with digital technologies to become more effective, competitive, and innovative.