Operations | Monitoring | ITSM | DevOps | Cloud
%term
IT Ops reporting is broken BigPanda Unified Analytics can help
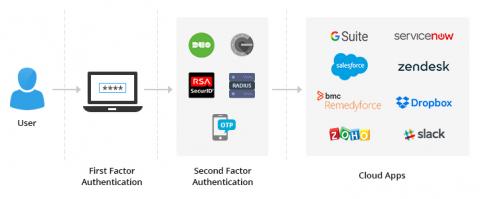
Thwart password spray attacks to secure employee access to cloud apps
Chances are you’ve heard of traditional credential-based attacks on Active Directory (AD) and cloud applications—brute force attacks, dictionary attacks, and keylogging, to name a few. There’s now another attack type you should familiarize yourself with: password spray attacks. In this blog, we’ll analyze why you should be wary of them and the best way to tackle them.
Internet of Things: The 3 Whys of IoT
The Internet of Things offers tangible benefits, but businesses lack diagnostic tools that provide real-time visibility into IoT performance problems.
Achieving Full Stack Automation Through Kubernetes
The open source revolution is back in full swing with the rise of Kubernetes. Flexibility and agility are the key factors to making the most of the cloud, multicloud, or hybrid cloud era. Kubernetes makes that easier by granting DevOps teams greater control across their infrastructure. But easier does not necessarily mean easy — there are still hurdles to overcome.
6 myths and facts about deep learning
Despite decades of development, deep learning has been boosted by the increasing processing power of computers and the immense amount of data available, which has allowed it to obtain some achievements that were unthinkable years ago. Deep learning is at the heart of what we know today as artificial intelligence. However, like everything that is talked about a lot, deep learning has formed a series of myths that do not always obey reality.
4 Business Disasters That Could Have Been Avoided With Real-Time Anomaly Detection
Digital, network-connected systems are transforming every aspect of business — from your mission-critical workloads to your most rarely used applications. But the increases in scalability and cost efficiency come at a cost. Because every system is so reliant on network connectivity, unplanned downtime is becoming increasingly expensive.
Cost Tracking For Serverless Architectures
Today we’ll talk more about the cost tracking for serverless architecture. Following the cost of serverless architecture utilization it might give you insights on how and what should you change or adapt to, to be able to reduce the cost. After all, we’re all always trying to improve our performances in every field while keeping the costs to a minimum (if possible).
5 Trends Transforming Digital and IT Operations Management
In 2018, digital transformation ushered in a radical shift in how enterprises harness customer insights, technology capabilities, and rapid experimentation to drive revenue growth, profitability, and market leadership. Enterprises spent $1.3 trillion in 2018 on digital transformation technologies like public cloud platforms, microservices and containers, edge computing, machine learning, and artificial intelligence to improve customer experiences, business agility, and employee engagement.
Logging Levels 101
If you’re a software developer, then you understand how vital application logging is in software development and a critical part of logging is something called logging levels. Log entries generally contain essential information—such as a timestamp, a message, and sometimes additional stuff like an exception’s stack trace. Those pieces of information are useful because they allow someone reading the log entry to understand how the application behaved in production.