Conquer it with correlation-Part 3: Cryptojacking
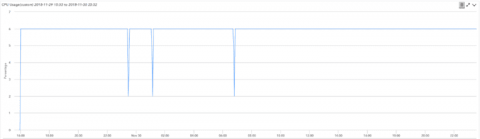
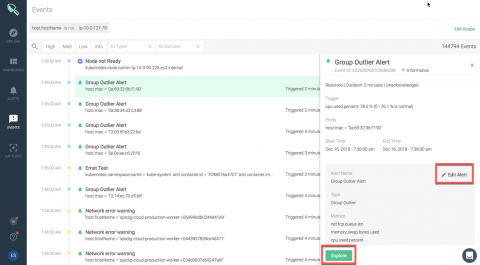
In the previous posts of this blog series, we discussed advanced persistent threats and data breaches, highlighting the importance of data security in today’s times. In the final post of this series, we’ll talk about cryptojacking, a type of attack that can severely affect your network’s integrity, and how you can combat it with event correlation.