Operations | Monitoring | ITSM | DevOps | Cloud
%term
Anodot
Launching Vulnerability Manager Plus: Hunt down security loopholes with 100% precision
Amp up your endpoint security game with ManageEngine’s all-new Vulnerability Manager Plus. Pinpoint, prioritize, and eliminate vulnerabilities with ease. Attackers are constantly coming up with new ways to carry out exploits, making it even harder for your organization to reduce its attack surface and keep its endpoints secure.
Message from Nexthink CEO
How to Filter Uptime.com Traffic From Google Analytics
Uptime.com checks can send more than a thousand visits to a URL each day as it monitors infrastructure metrics. Checks record load times and tell administrators which elements are causing slowness. Basic HTTPS checks are the most common, checking for outages and recording downtime or providing technical data to fix them.
Alerting with Stackdriver - Stack Doctor
Introducing the LogicMonitor - ServiceNow CMDB Integration. Let's get started.
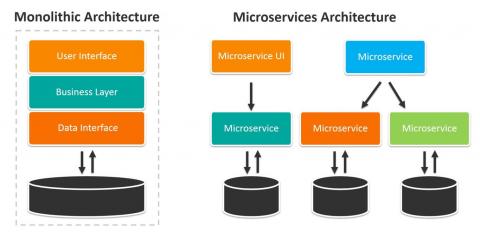
Microservices vs. Monolithic Architectures
Enterprises are increasingly pressured by competitors and their own customers to get applications working and online quicker while also minimizing development costs. These divergent goals have forced enterprise IT organization to evolve rapidly. After undergoing one forced evolution after another since the 1960s, many are prepared to take the step away from monolithic application architectures to embrace the microservices approach.
Top 6 Container Security Lessons from Deploying Kubernetes and Red Hat OpenShift
We recently had the opportunity to share the lessons we have learned about container security from deploying Kubernetes and OpenShift in the field. If you don’t have time to watch the full recording of our conversation, here are a few highlights.
How to handle AWS Lambda cold starts
Smarter people than myself, once said that you should do things you don’t like first so that you can enjoy the things you’re doing later. Nobody wants cold starts. They’re annoying, and we continuously feel an itching sensation in our brains because of them. The serverless world would be a much better place to work in if they weren’t there.