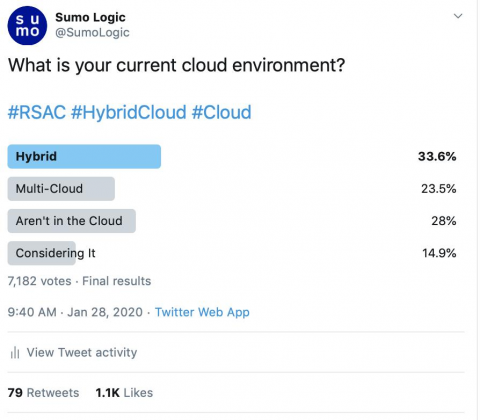
Pre-RSA Twitter Poll: 3 Interesting Observations on SOC, SIEM and Cloud
In advance of the RSA Conference 2020, we wanted to get a pulse of attendees’ perceptions on a few topics, specifically challenges facing modern SOCs (security operations centers) and the value they are getting from technologies such as analytics, automation, and their SIEM tools. To get this, we fielded a series of questions to the Twitter-verse and received nearly 17,000 votes! After going through the results, we found a few interesting things…