Operations | Monitoring | ITSM | DevOps | Cloud
%term
Building a resilient cybersecurity strategy for 2019 - Part 2
Using Logs for Troubleshooting
Logz.io - Who We Are and What We Do
Setting Up Application Performance Monitoring with the ELK Stack and Logz.io
Application Performance Monitoring, aka APM, is one of the most common methods used by engineers today to measure the availability, response times and behavior of applications and services. There are a variety of APM solutions in the market but if you’re familiar with the ELK Stack or are a Logz.io user, this article describes using a relatively new open source-based solution — Elastic APM.
SolarWinds Adds Access Rights Management to Its IT Management Portfolio, following the Acquisition of 8MAN
LogDNA Custom Parsing Webinar
What is CI/CD?
This article describes how continuous integration, delivery, and deployment can help development teams build and release software quickly and reliably.
Kubernetes: Securing Hybrid and Multi-Cloud Environments
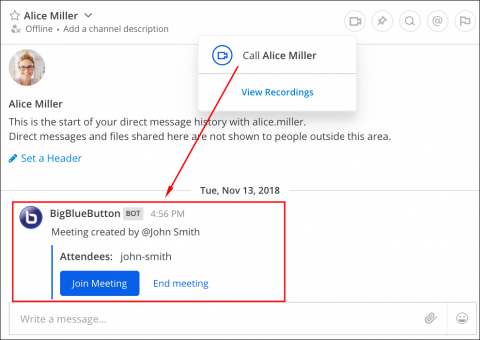
BigBlueButton integration brings powerful web conferencing tools to Mattermost
BigBlueButton is an open source web conferencing system. The product enables real-time sharing of audio, video, slides and screens, with collaborative capabilities such as shared whiteboard, polling and breakout rooms. Blindside Networks, the company behind the BigBlueButton project, has created a plugin that brings all of these collaborative capabilities within Mattermost.