Operations | Monitoring | ITSM | DevOps | Cloud
October 2019
Beware of black cats and black hats this Halloween
It’s that time of the year again when you sport your favorite costume, carve pumpkins, gear up for trick-or-treating, and reread Gothic stories. It’s almost Halloween! There is no denying that October is all about ghosts and ghouls, tricks and treats, witches and wizards, pirates and pumpkins. However, October is also National Cybersecurity Awareness Month (NCSAM), a time to remember that alongside our cogent fears lies another reality that’s much more ghastly—cyberattacks.
Five worthy reads: Cybersecurity drift: Leveraging AI and ML to safeguard your network from threats
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, sticking with October’s cybersecurity awareness theme, we’ll take an in-depth look at both the good and the bad of artificial intelligence (AI) and machine learning (ML) in cybersecurity.
IT analytics in 90 seconds: Easily detect security breaches in your privileged accounts
Monitor these loopholes to ensure complete network security
The continuous evolution and growth of the endpoint devices in enterprises makes network security management a primary concern for IT departments. As a sysadmin, you strive to ensure the safety and security of every device in your network. You are on a constant lookout for vulnerabilities and issues that might disturb the shield that protects your enterprise devices. With dynamically changing trends and technologies, it’s easy to miss details that might compromise your network’s armor.
12 mobile device features that help ensure corporate data security
Our hearts might skip a beat every time we put our hands in our pocket and can’t find our mobile phone, and we’re filled with dread at the thought of losing the device that contains our personal photos and the corporate data saved on it. But just misplacing a device is not how we put corporate data at risk; small actions in our day-to-day lives can have a major impact on the safety of the corporate data on our devices.
Introducing the Wi-Fi Analyzer for OpManager's Android app: A perfect team for sustained IT infrastructure management
Addressing Wi-Fi issues can be challenging Tracking the availability, speed, and performance of a large number of systems, servers, VMs, routers, access points, firewalls, interfaces, and WAN links, plus monitoring their health is not a simple task. Tackling angry emails from employees about Wi-Fi running slowly, or it taking a lifetime to download a simple setup file or load a business-critical application, can hamper productivity.
Combating threats with UEBA: Money matters
In this four-part series, we explore hypothetical cyberattacks inspired by real-life events in four different industries: healthcare, finance, manufacturing, and education. We’ll take a look at unforeseen security attack scenarios, and discover how user and entity behavior analytics (UEBA) can be leveraged to safeguard organizations. In this second post of the series, we’ll examine cyberattacks that threaten the financial sector.
Trick-or-treat down Halloween Cyber Street for cyber awareness
Halloween is perhaps the one night of the year where ghosts and ghouls roam freely on the streets. In reality, these are all just harmless children in costume; however, as you enter Halloween Cyber Street, you’ll come to find there are real threats lying in wait for an opportunity to strike. On Halloween Cyber Street, there are eight houses, each providing a webinar offering solutions on how you can protect yourself against different cyberthreats.
IT analytics in 90 seconds: How to manage your privileged accounts' passwords like a pro
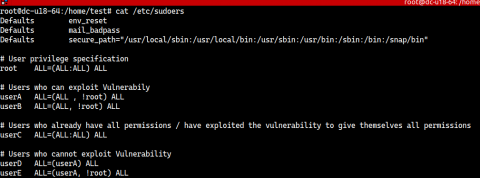
A catastrophic flaw in Linux sudo command with a simple fix using Desktop Central
A critical vulnerability in sudo has been disclosed, that when exploited, enables users to bypass security restrictions and execute commands as the root user. This security flaw has to be swiftly remediated as sudo is one of the most integral and commonly used functionalities in Linux operating systems.
ServiceDesk Plus introduces IT Release Management
We’re proud to announce the latest feature in ServiceDesk Plus Cloud: IT Release Management. This new capability helps you build, test, and deliver IT software releases with minimal risks and greater transparency.
More Android malware and another iOS exploit: How to safeguard your devices?
The past few months have seen both Android and iOS fall prey to various security attacks, with more malware attacks and exploits being uncovered on a daily basis. First, let’s look at the newest zero-day Android vulnerability. This vulnerability leverages the ”use-after-free” memory flaw to wreak havoc on mobile devices. In layperson terms, the use-after-free flaw allows access to memory recently freed (after performing some operation) to execute malicious code.
IT analytics in 90 seconds: Track anomalies in your privileged account activity
Android malware: How do enterprises tackle this ever-growing menace?
Let us first agree on a couple of things before we start: One, Android is the most affordable platform for enterprises with a mobile-first/mobile-only workforce, and it has the smallest learning curve of any mobile OS. Two, due to its very open-source nature, Android is easy for malicious actors to pray on, with the Google Play Store being the breeding ground for many attacks.
Announcing ServiceDesk Plus 11.0 with rapid-start enterprise service desk capabilities
In late 2017, we announced enterprise service management (ESM) capabilities for our cloud model of ServiceDesk Plus. It helps organizations worldwide create unique service desk instances for each of their business functions like HR, travel, and facilities, and manage service delivery across their enterprise from a central platform. Now, we’ve expanded our ESM footprint to our on-premises model of ServiceDesk Plus.
The Rapid-start Enterprise Service Desk
IT analytics in 90 seconds: Monitor privileged account permissions to mitigate insider threats
WSUS: The outdated way of staying updated?
WSUS (Windows Server Update Service) is an add-on provided by Microsoft for patching Windows applications. Along with being free, the basic functionalities that WSUS provides makes it an easy choice for major SMBs. However, in reality, WSUS falls short in a number of ways; because of this, many teams that rely on WSUS for their patching needs end up investing in additional tools that usually come at an additional cost.