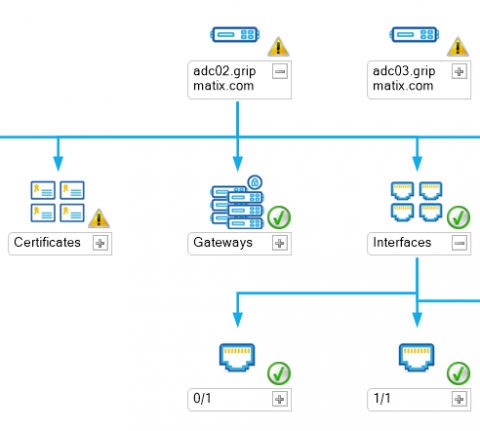
Doing more with less in IT, yes this impacts Citrix teams too!
If you work in a technology role, then it won’t be any surprise to you when I say organizations have pivoted from specialist IT job functions, such as Citrix only roles, to making sure the infrastructure team can support many workloads. The adoption of cloud technologies has also created support for this approach because our infrastructure teams are doing less architecting and more application configuration and user work.