Operations | Monitoring | ITSM | DevOps | Cloud
Containers
The latest News and Information on Containers, Kubernetes, Docker and related technologies.
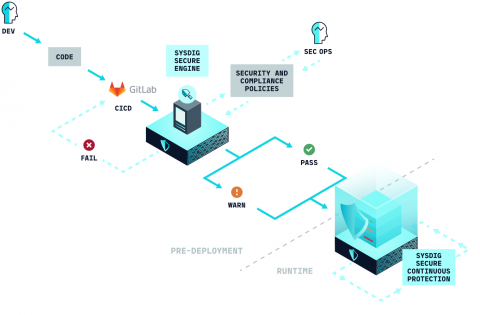
Integrating Gitlab CI/CD with Sysdig Secure
In this blog post we are going to cover how to perform Docker image scanning on the Gitlab CI/CD platform using Sysdig Secure. Container images that don’t meet the security policies that you define within Sysdig Secure will be stopped, breaking the build pipeline before being pushed to your production Docker registry.
Kubernetes & Tigera: Network Policies, Security, and Auditing
Meeting PCI DSS Network Security Requirements in Kubernetes Environments
How To Extend Firewalls to Kubernetes to Stop Breaking Existing Security Architectures
Why Can't We Be Friends? - Kubernetes in a Zone-Based Architecture World
Getting started with Jaeger to build an Istio service mesh
Service mesh provides a dedicated network for service-to-service communication in a transparent way. Istio aims to help developers and operators address service mesh features such as dynamic service discovery, mutual transport layer security (TLS), circuit breakers, rate limiting, and tracing. Jaeger with Istio augments monitoring and tracing of cloud-native apps on a distributed networking system.
Automated Containerization of Apps Using CloudHedge
Well, the answer is yes and no. Containerization is a relatively new technology and needs significant efforts to containerize an application, orchestrate, secure, manage and monitor it. Hence it’s worth looking at what does it take to containerize, deploy and run an application in real production in bit details for you to take a call whether you want to venture into it yourself or not.
Kubernetes Master Class: Using Persistent Storage in Kubernetes and Project Longhorn
CI/CD/Civo/C-what?
As a cloud provider and DevOps-focused company, we definitely want to practice what we preach. We see the benefits of a modern cloud native architecture, so we built our hosting of www.civo.com and api.civo.com (our application) to take full use of these modern decisions. This post describes our approach to Continuous Integration (CI) and Continuous Deployment (CD) from a Chief Technical Officer's perspective.