Applying Zero Trust to Data Centre Networks
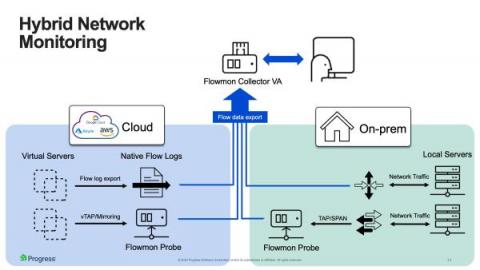
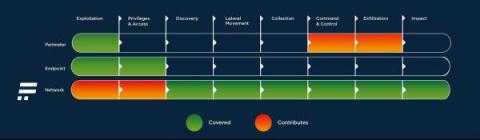
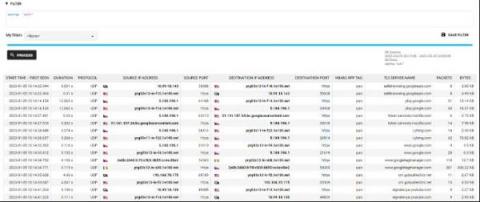
Zero trust isn’t an approach that can be delivered by buying a single product that claims to provide it. Instead, it is an approach that needs to be understood and implemented in complementary ways across an organization’s IT systems. We recently hosted a webinar titled Applying Zero Trust to Data Centre Networks to provide guidance on how organizations can use zero trust to enhance the security of their IT systems. The webinar details are below, after a summary of the topics covered.