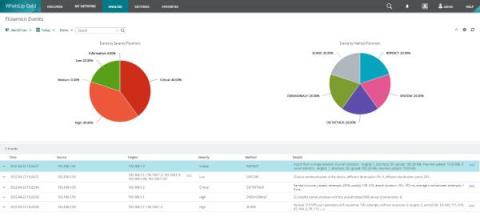
Flowmon Anomaly Detection & MISP
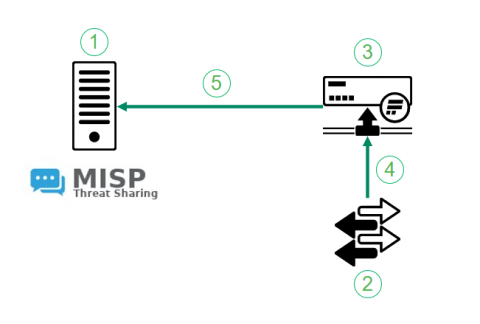
Back in 2021 we have introduced the integration between MISP, a community threat intelligence sharing platform and Flowmon ADS. The integration turns indicators of compromise shared through MISP to actionable intelligence. Flowmon ADS will automatically pick up on latest indicators of compromise using MISP API and leverage those indicators of compromise to detect adversary activities in the target network. The integration is available in Flowmon ADS 11.2 and newer versions.