Ransomware in 2021: What has changed? Detection and mitigation strategy
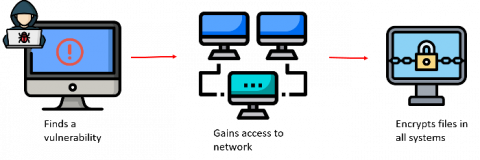
A ransomware attack is a bug that we can’t shake off. Or perhaps, it can even be called a shape-shifter that somehow finds a way into networks, no matter how many armed sentries you’ve deployed in and around your perimeter. The line between ransomware and a data breach is slowly fading. Threat actors prefer ransomware over other modes of attack because they work.