How to monitor IIS effectively
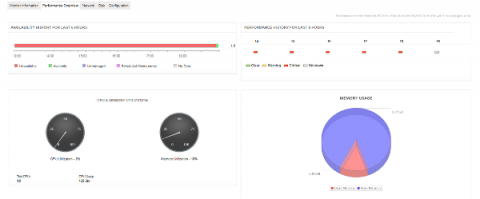
Microsoft Internet Information Services (IIS) is a popular web server for hosting web applications and is widely used in many sectors, such as healthcare, banking, e-commerce, logistics, etc. The IIS web server is the backbone of many IT infrastructures. But if the IIS web server encounters problems, it can lead to websites and applications experiencing higher response times, and timeouts resulting in end-users either leaving your website or complaining about the performance.