What is modern management, and how will it revolutionize enterprise IT management?
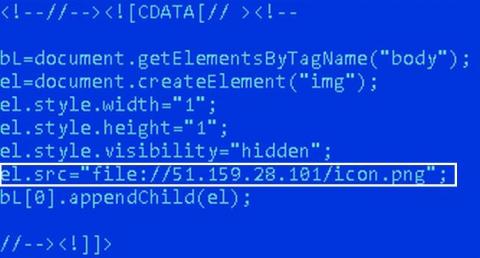
IT departments have experienced numerous changes in the way they manage and control user devices. Starting with the traditional CRT monitor-based computers, to modern smartphones, technological developments have been remarkable. Additionally, with the COVID-19 pandemic, employees are restricted to work from home, making the IT administration routines challenging for system administrators.