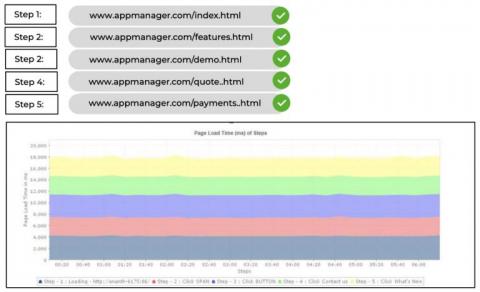
File shadowing: The key to a swift recovery from USB and file-based attacks
USB devices are undeniably valuable, but they can be dangerous. On one hand, they are useful in transporting enterprise-critical data, but on the other, they can wreak havoc if misplaced, corrupted due to a human or hardware-related error, or stolen. It’s no wonder some companies forbid the use of USB devices altogether.