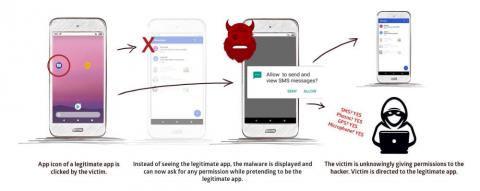
StrandHogg vulnerability threatens 500 of the most popular Android apps
Earlier this month, security researchers at Promon, a Norwegian firm that specializes in in-app security, uncovered a unique vulnerability in Android devices that allows malicious apps to masquerade as legitimate apps and prompt for intrusive permissions that allow them to: Listen to the user through the microphone, Take photos using the camera, and a lot more.