IT Risk Assessment vs. IT Risk Management: The Difference and What They Mean to the Service Desk
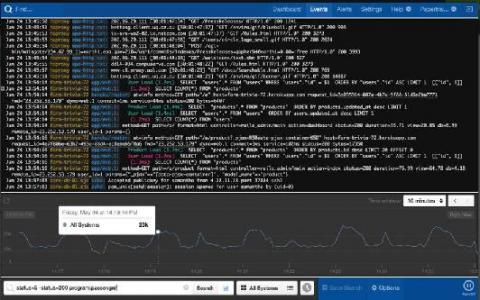
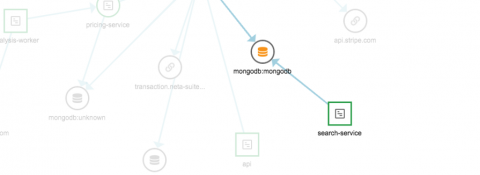
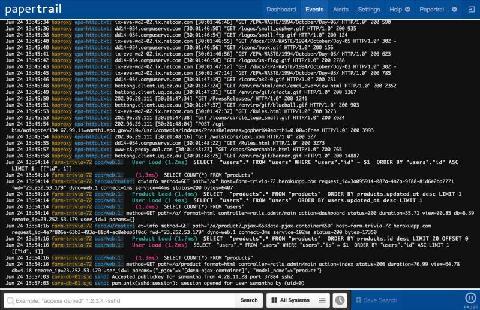
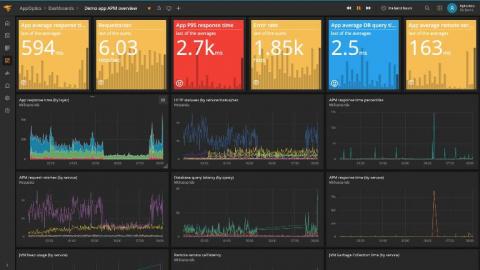
In life, risks can be perceived both negatively and positively. Taking a risk can sometimes yield great results, but other times, a risk is a yellow light of caution. For businesses in particular, if not managed properly, IT risks like malware malfunctions and employee errors can range in size and occur in several areas. The result is disruption and valuable time being used to resolve the issue. But even with risk present, there are measures IT can put in place to ward them off.