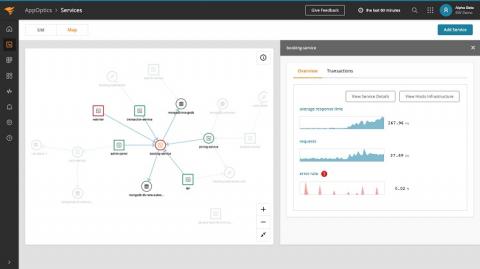
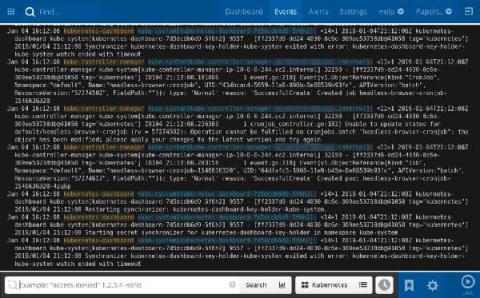
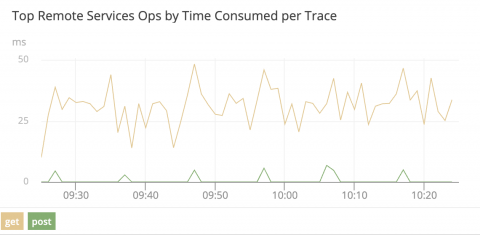
SolarWinds Updates APM Suite Designed to Simplify Application and Infrastructure Management
Introduces new service map and web transaction recorder, enhanced custom parsing rules, and search user experience to further reduce application performance management complexity and speed up troubleshooting.