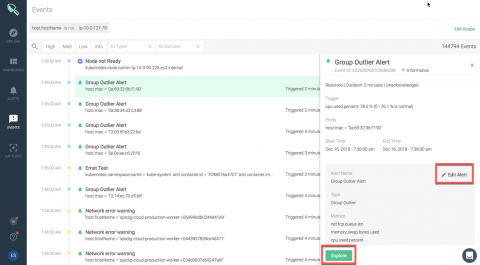
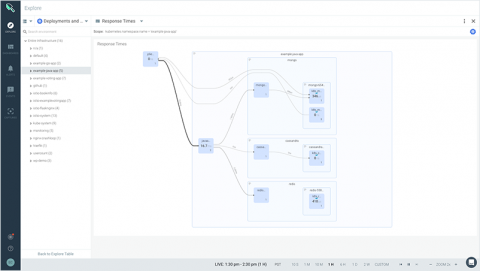
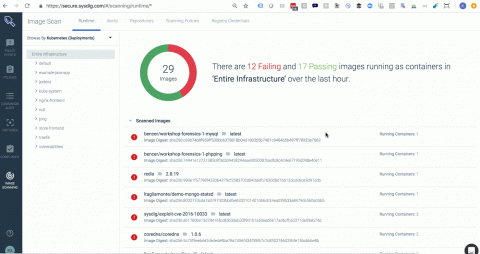
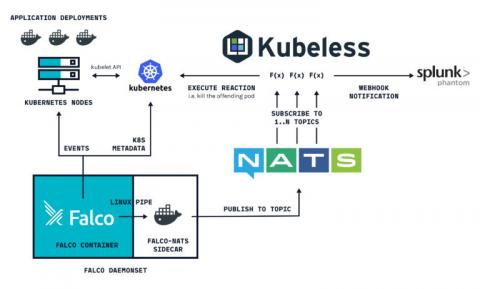
Unveiling Sysdig Monitor Events
At Sysdig, we have built a cloud-native intelligence platform to create a single, more effective way to monitor and secure your critical applications. We want to empower our users to quickly identify critical events and focus on events that need the most attention from you.