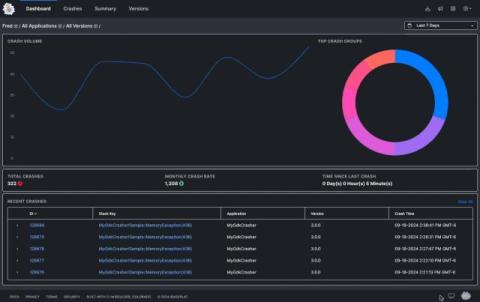
Network monitoring, explained
Network monitoring continuously observes and manages the performance, availability, and security of a computer network to identify issues before they affect operations. As IT infrastructure grows more complex, network monitoring ensures your business stays online, whether dealing with on-premises or cloud environments. In hybrid or multi-cloud settings, having visibility across all systems is crucial to maintain seamless performance and prevent disruptions.