How the kubernetes community responded to the k3s launch
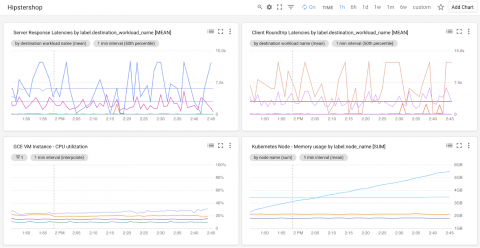
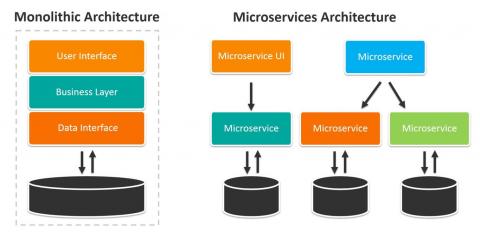
What an amazing first week! I’ve been marketing open source technologies for over 15 years. During that time, I’ve been involved in many new product releases. Nothing comes close to the response we’ve had from k3s – http://k3s.io. Judging by the incredible feedback (including over 4,500 GitHub stars in one week), the release of k3s appears to have landed at exactly the right time.