Operations | Monitoring | ITSM | DevOps | Cloud
Linux
Cloud PaaS through the lens of open source - opinion
Open source software, as the name suggests, is developed in the open. The software can be freely inspected by anyone, and can be freely patched as required to suit the security requirements of the organisation running it. Any publicly identified security issues are centrally triaged and tracked.
DataOps: keeping the data flowing with Model-driven Operations
If you’ve ever lived DataOps, you’ll know that it’s a challenge at the best of times. A day in the life of a typical data engineering team involves securing, releasing, debugging and stabilising complex and oftentimes fragile data pipelines. These pipelines can involve many source applications and intermediaries, and troubleshooting them under management pressure when it’s all going wrong is stressful.
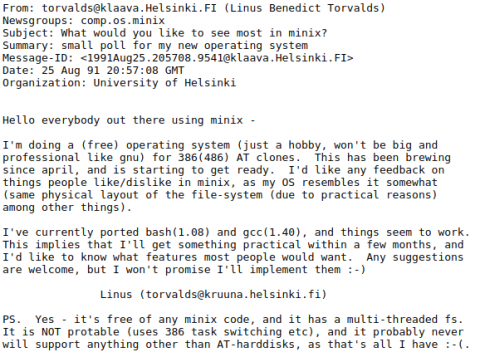
We Celebrate Linux Turning 30!
Happy birthday - 30 Years of Linux
Thirty years ago today, Linus Torvalds announced his free operating system to the world. As with many of the world’s greatest, Linux had humble beginnings as a very small pet project. The GNU was working on an ambitious free, public domain operating system but the project had been delayed, and enthusiasts were quick to adopt Linus’ new project.
eBPF: When (and when not) to use it
Extended Berkeley Packet Filter (eBPF) is a relatively new feature for Linux kernels that has many DevOps, SREs, and engineers excited. But is it a one-stop shop solution for all of your Linux kernel needs? Let’s take a look at what eBPF does well, and how it stacks up against standard Linux iptables.
Kubernetes Fully Managed - half the cost of AWS
How can you run a fully managed Kubernetes in a private cloud at half the cost of Amazon EKS (Elastic Kubernetes Service)?
The State of Robotics - July 2021
From autonomous mobile robots to robot butlers. It is impressive to see how much progress has been made in the last decade. Thanks to our open source robotics community we keep learning, and this newsletter is filled with events, R&D updates, new products and tutorials for you. Thanks July!
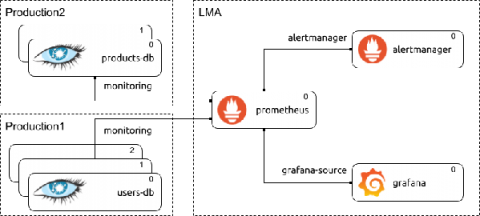
Model-driven observability: the magic of Juju topology for metrics
In the first post of this series, we covered the general idea and benefits of model-driven observability with Juju, but did not dive deep into the idea of contextualization and how it makes observability more actionable. In this post we start addressing what contextualization means in model-driven observability, starting from adding Juju topology metadata added to telemetry, and how that improves the processing and querying the telemetry for charmed applications.
How to detect security threats in your systems' Linux processes
Almost all tasks within a Linux system, whether it’s an application, system daemon, or certain types of user activity, are executed by one or more processes . This means that monitoring processes is key to detecting potentially malicious activity in your systems, such as the creation of unexpected web shells or other utilities.