Operations | Monitoring | ITSM | DevOps | Cloud
%term
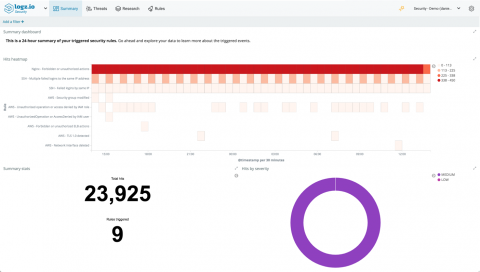
Combining Threat Detection with Artificial Intelligence, Logz.io Launches Security Analytics App for ELK Stack on its Continuous Operations Platform
Boston and Tel Aviv, October 24, 2018 — Logz.io, the leader in AI-powered log analysis, releases the first robust security application built on the open source ELK Stack, bringing powerful and scalable security monitoring and analysis directly into the DevOps workflow.
A Deeper Dive into Logz.io Security Analytics
Facing the growing threat of cybercrime, and to answer compliance requirements, more and more organizations are looking at their DevOps and Operations teams to implement security. The term “security”, however, often triggers negative feelings among engineers. The reason for this is that security is associated with siloed, sequential and complicated processes — all roadblocks to fast development and deployment.
Announcing Logz.io Security Analytics
We founded Logz.io four years ago with a vision to provide a platform for engineers like us to operate the next generation of applications and infrastructure. As engineers, we experienced firsthand the challenges of running large-scale, open-source tools and the frustration of dealing with slow, proprietary tools which were not designed to support the rapidly changing technology stack we operated.
Test Automation Tools to Accelerate CI/CD
So much of our world has moved away from the slow and methodical, towards the agile and iterative. In transport, for example, everything is “on demand”, constantly changing and adaptable. The same is true for developers. With movements and philosophies such as CI/CD, everything is about moving quickly, yet smartly. Test automation is an integral part of this development philosophy.
Splunk Everywhere! State and Local Government
How Many Packets per Second (PPS) in Amazon EC2?
A customer of ours reported a limit on number of packets in Amazon’s EC2 instances. According to the report, it didn’t happen on all instance types, and didn’t happen all the time. Also, it was unrelated entirely to bandwidth or MTU. According to the report, packet transmission rates were limited the same as CPU on t2/t3 instances — each instance earns credits which, when exhausted, cause throttling.
October 2018 Online Meetup: Migrating from Rancher 1.6 to Rancher 2.1
CloudReady Dashboards Tips & Tricks Part #2
This is the second part of a series on the CloudReady dashboards and visualizations. The first part covered basics like Overviews, Refresh, and Layout settings. In this second part, we’ll cover more advanced creation and usage of dashboards. In part 3 and 4 we’ll cover actual widgets and how they can be used.
DNS Monitoring: A Necessary Task.
When we think of DNS (Domain Name System), there are two thoughts that we all assume to be true and that become natural justifications for the development of a DNS Monitoring scheme.Simple and forceful, in fact since the rise of the Internet, DNS systems are a fundamental part of our communications.