Operations | Monitoring | ITSM | DevOps | Cloud
Active Directory
Advanced Active Directory attacks: Simulating domain controller behavior
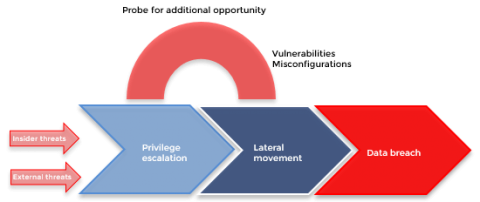
There was a time when cyberattacks on identity and authentication infrastructures [like Active Directory (AD)] were immensely challenging to perform. A lot of forethought had to be put into devising a plan for the careful execution of attacks, and advanced technical knowledge of domains and networks was a requisite. Over time, with the advent of open-source pen testing tools, the knowledge gap and the complexities involved to carry out a full-scale cyberattack have narrowed drastically.
Integrating Flowmon and LDAP/AD
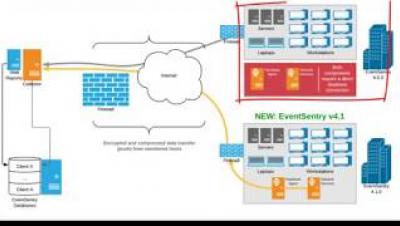
The integration of Flowmon with an external user database such as Active Directory (AD) significantly simplifies access rights management both for small companies and enterprises. Although it has been available for some time, there are some helpful functions that may not be immediately obvious.
The LLMNR/NBT-NS strike
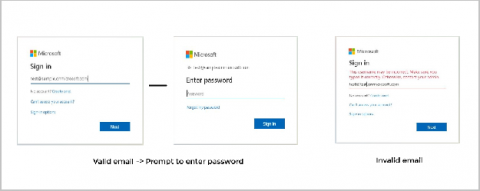
Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Service (NBT-NS) are two protocols that are used to identify a host address on a network when the DNS name resolution, which is the conventional method, fails to do so. When a DNS server is unable to resolve a request from a requester machine, the latter broadcasts a message to its peer computers asking for the location of the required server. Hackers leverage this operation to steal the credentials of the requester machine.
Permissions, access rights, and privileges: Active Directory and Azure Active Directory
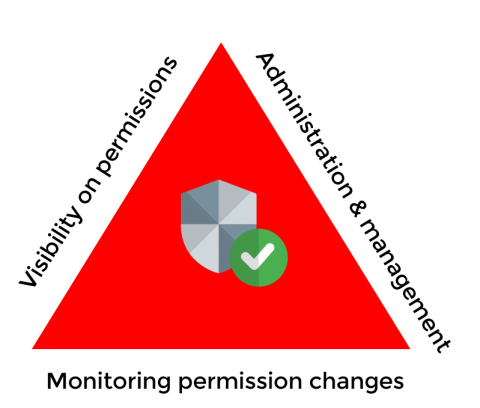
Permissions, access controls, user rights, or privileges define what an identity can see or do in an organization. These terms are often used interchangeably based on context, and essentially perform the same function—granting or denying access to the resources in an enterprise.
Monitoring Applications That Use Azure ADFS
ADFS (Active Directory Federation Services) is a solution from Microsoft for single sign-on (SSO) functionality. It is used by organizations that have their users on Windows Servers to provide authentication and authorization to web-based applications or services outside the organization. ADFS implements federated identity and claim-based access control to authenticate and authorize users, thus maintaining security.
Securing Azure Active Directory from PowerShell abuse
Malware attacks are evolving and once common tactics are becoming a thing of the past. Attack strategies, like using a third-party hacking program or injecting viruses from external sources, are almost obsolete as they leave a distinct footprint. Most antimalware tools can now detect the presence of a foreign program or device and immediately block them.
SCOM alert tuning tips from the masters Webinar 27-Mar-20 - tips for AD, SQL, Oracle and SCOM itself
DataSource Spotlight: Proactive Visibility of LDAP Security
At LogicMonitor, we believe our platform enables our customers to See More, Know More, and Do More, to keep up with the rapid pace of change in business today. The following is an interesting use case that illustrates how LogicMonitor can provide quick insight to enable modern IT teams to work proactively and perform at maximum operational efficiency.