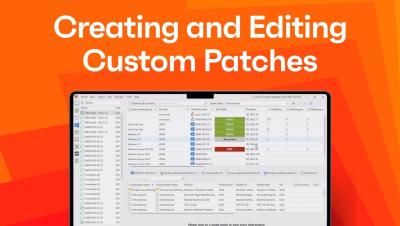
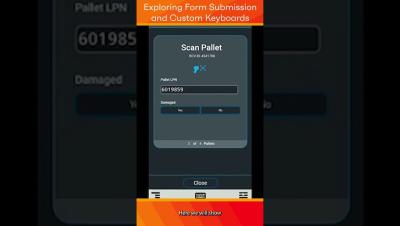
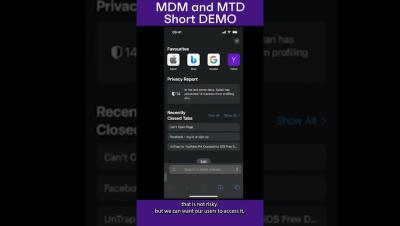
Optimizing the Retail Returns Process
January often means the longest lines in the retail store are for returns. And, maybe ironically, those returns are regularly processed at the Customer Service desk. That right there — that’s an annual challenge. Consumers entering a store to make a return or exchange are already feeling inconvenienced. They bought or received an item they can’t use, and they’re at the store to resolve that problem.