What is a Failover Cluster? How It Works & Applications
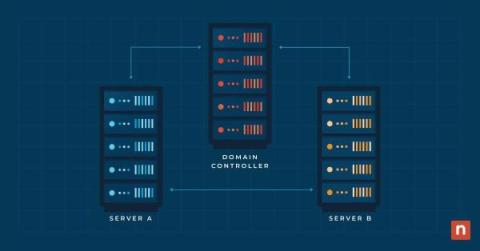
Seamless operations and system resilience are critical concerns in modern business IT, and failover cluster technology can play a major role in achieving these goals. This article delves deep into the core of failover clusters, exploring their functionality and applications. Whether you’re a seasoned IT professional or a curious enthusiast, read on to understand the intricacies of failover clusters, discover how they work, and see scenarios where they prove indispensable.