Operations | Monitoring | ITSM | DevOps | Cloud
Splunk
A Picture is Worth a Thousand Logs
Splunk is a fantastic platform for ingesting, storing, searching and analysing data from logs, metrics and traces from a massive variety of sources. But does that mean we should ignore all of that data that doesn’t fall into these categories, like image and video data for example? Of course not!
Observability and Monitoring for Modern Applications
I drive a 2005 Ford diesel pickup truck. Most of the time my truck runs great. But occasionally an orange light on the dashboard will flicker on to alert me that something is wrong. Unfortunately, there’s no information about what is wrong and why. My truck has a monitoring solution, but not an observability solution. In many cases, IT has the same problem as my truck.
Hyperledger Besu is an Observability Pioneer
All the work presented in this blog post is open source and available as part of our Splunk Connect for Ethereum repository examples, including the instrumentation of Besu as a Docker container, the configuration of Splunk, and two applications showing how to monitor Besu syncing to the chain.
Detecting HAFNIUM Exchange Server Zero-Day Activity in Splunk
If you want just to see how to find HAFNIUM Exchange Zero-Day Activity, skip down to the “detections” sections. Otherwise, read on for a quick breakdown of what happened, how to detect it, and MITRE ATT&CK mappings.
Building a Superstar SOC with Automation and Standardization
When you have a team of security analysts that have a wide range of expertise, knowledge, and experience, it is natural to see the difference in the quality of work performed. One of the biggest challenges that security operation managers face when auditing the work performed is that some team members may execute different steps at different levels of rigor when investigating and remediating threats.
From the SecOps Kitchen: Why Operators of Essentials Services Need to Prepare Now
Hey there, The European Union Agency for Cybersecurity (ENISA) has recently published its NIS Investment report - a survey conducted on European organisations identified as Operator of Essentials Services (OES) and Digital Service Providers (DSP).
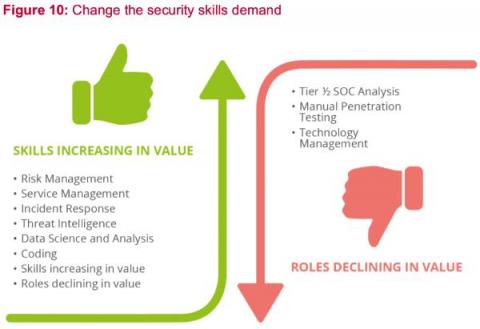
As Funding Cuts Arrive, Can CDM Deliver on the Value of Its Promises?
For anyone who works in cybersecurity, getting a tough job done with severely limited resources is all in a day’s work. But when funding allocations suddenly shift after essential programs are already under development, it can be hard for even the most creative, resilient CIOs and CISOs to keep up.
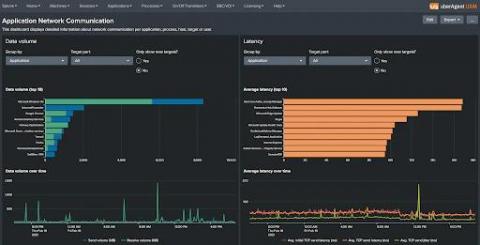
Enriching Splunk Contact Center Analytics with uberAgent Endpoint Monitoring
Like many other industries, contact centers are increasingly relying on employees working from home. The WFH trend poses new challenges, but it also surfaces issues that were largely ignored before. This article explains how holistic monitoring with Splunk Contact Center Analytics and uberAgent help drive exceptional customer service.
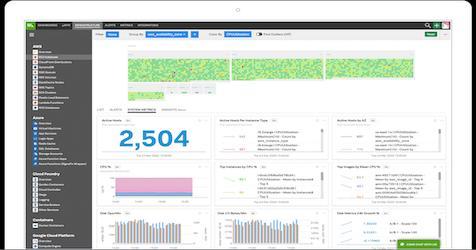
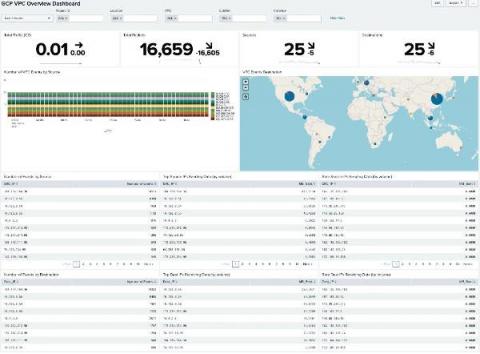
Exploring the Value of your Google Cloud Logs and Metrics
With our ability to ingest GCP logs and metrics into Splunk and Splunk Infrastructure Monitoring, there’s never been a better time to start driving value out of your GCP data. We’ve already started to explore this with the great blog from Matt here: Getting to Know Google Cloud Audit Logs. Expanding on this, there’s now a pre-built set of dashboards available in a Splunkbase App: GCP Application Template for Splunk!