Operations | Monitoring | ITSM | DevOps | Cloud
Splunk
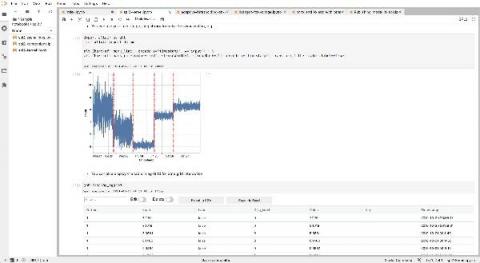
Getting to Know Google Cloud Audit Logs
So you've set up a Google Cloud Logging sink along with a Dataflow pipeline and are happily ingesting these events into your Splunk infrastructure — great! But now what? How do you start to get meaningful insights from this data? In this blog post, I'll share eight useful signals hiding within Google Cloud audit logs that will help you uncover meaningful insights. You'll learn how to detect: Finally, we’ll wrap up with a simple dashboard that captures all these queries in one place.
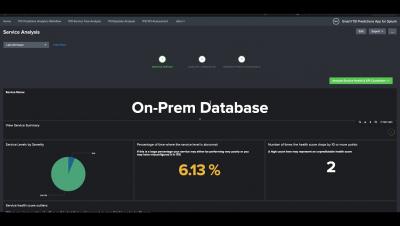
Smart ITSI Insights App for Splunk
Visual Link Analysis with Splunk: Part 1 - Data Reduction
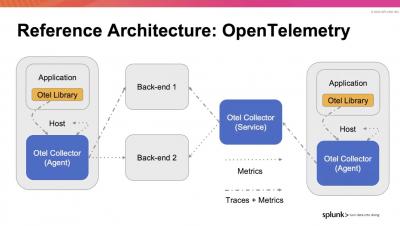
Recently, I presented at .conf20, Splunk’s annual user conference, on link analysis, where I promised more technical details on the topic in the coming weeks. To keep my promise, I’ve started a three-part series to show you how to use Splunk for link analysis.
Walkthrough to Set Up the Deep Learning Toolkit for Splunk with Amazon EKS
The Splunk Deep Learning Toolkit (DLTK) is a very powerful tool that allows you to offload compute resources to external container environments. Additionally, you can use GPU or SPARK environments. In last Splunk blog post, The Power of Deep Learning Analytics and GPU Acceleration, you can learn more about building a GPU-based environment. Splunk DLTK supports Docker as well as Kubernetes and OpenShift as container environments.
Get to Know Splunk Machine Learning Environment (SMLE)
One of our most exciting new projects at Splunk is coming to life. Over the past year, we have been hard at work putting together our vision: a place where Splunk admins, NOC/SOC teams, data analysts, and data scientists can collaborate, experiment, and operationalize their work, all in a single environment inside the Splunk ecosystem. We call it Splunk Machine Learning Environment (SMLE).
Splunk SOAR Playbooks: Finding and Disabling Inactive Users on AWS
Every organization that uses AWS has a set of user accounts that grant access to resources and data. The Identity and Access Management (IAM) service is the part of AWS that keeps track of all the users, groups, roles and policies that provide that access. Because it controls permissions for all other services, IAM is probably the single most important service in AWS to focus on from a security perspective.
What's Next for Department of Defense Digital Modernization?
As the Trump Administration comes to a close, there is no better time than the present to reexamine the Department of Defense Digital Modernization Strategy and its potential sustainment beyond January 2021.
Macros, We Don't Need No Stinking Macros! - Featuring the New Microsoft O365 Email Add-On
Recently, I’ve been on a mission building a new Microsoft Office 365 Email Add-on for Splunk. This has been built for use with Splunk Enterprise, while making sure that it properly supports Splunk’s Common Information Model (CIM). CIM is paramount when wanting data to play nicely with Splunk Enterprise Security.