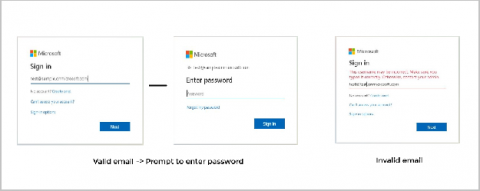
Securing Azure Active Directory from PowerShell abuse
Malware attacks are evolving and once common tactics are becoming a thing of the past. Attack strategies, like using a third-party hacking program or injecting viruses from external sources, are almost obsolete as they leave a distinct footprint. Most antimalware tools can now detect the presence of a foreign program or device and immediately block them.