Operations | Monitoring | ITSM | DevOps | Cloud
Technology
The latest News and Information on APIs, Mobile, AI, Machine Learning, IoT, Open Source and more!
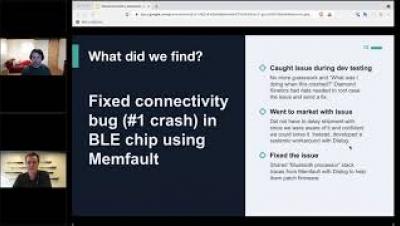
Remote Debugging & Device Observability: How Memfault & Diamond Kinetics fix firmware bugs together
5 Most Common API Errors and How to Fix Them
As software got more complex, more and more software projects rely on API integrations to run. Some of the most common API use cases involve pulling in external data that’s crucial to the function of your application. This includes weather data, financial data, or even syncing with another service your customer wants to share data with. However, the risk with API development lies in the interaction with code you didn’t write—and usually cannot see—that needs debugging.
Detecting unusual network activity with Elastic Security and machine learning
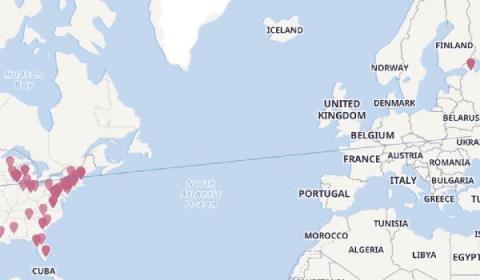
As we’ve shown in a previous blog, search-based detection rules and Elastic’s machine learning-based anomaly detection can be a powerful way to identify rare and unusual activity in cloud API logs. Now, as of Elastic Security 7.13, we’ve introduced a new set of unsupervised machine learning jobs for network data, and accompanying alert rules, several of which look for geographic anomalies.
Announcing the GA of the LogDNA Configuration API and LogDNA Terraform Provider
We’re excited to announce that our Configuration API and Terraform Provider are now generally available for all LogDNA customers. We received tremendous feedback from our public beta release and, based on that feedback, we are enabling several new features with the GA release that allow for more programmatic workflows with LogDNA. First, we are enabling Preset Alerts as a new resource that can be configured with the configuration API as well as within Terraform.
7 paw-some traits you didn't know about Freddy AI
From notebooks to pipelines with Kubeflow KALE
Kubeflow is the open-source machine learning toolkit on top of Kubernetes. Kubeflow translates steps in your data science workflow into Kubernetes jobs, providing the cloud-native interface for your ML libraries, frameworks, pipelines and notebooks. Read more about Kubeflow
AI in Predictive Maintenance and Forecasting
Industry 4.0 is taking every industry by storm with unprecedented advancement with innovative technology solutions. Its key technologies such as automation, AI, ML, Data Analytics and IoT enables industries to drive business operations with automated data-driven intelligence. Integrating the physical and digital systems, the manufacturing industry is increasingly adopting intelligent manufacturing in this Industry 4.0 era.
IT Remote Monitoring Software
I’ve recently been talking to some of the users of our eG Enterprise monitoring solution and its AIOps-powered root cause analysis platform. Multiple users have mentioned how the usability of the solution has been enhanced considerably by the availability of rich featured mobile apps for iOS and Android platforms.
Defending the Internet of Things from hackers and viruses
The 2010 Stuxnet malicious software attack on a uranium enrichment plant in Iran had all the twists and turns of a spy thriller. The plant was air gapped (not connected to the internet) so it couldn’t be targeted directly by an outsider. Instead, the attackers infected five of the plant’s partner organizations, hoping that an engineer from one of them would unknowingly introduce the malware to the network via a thumb drive.