Improving the Signal-to-Noise Ratio in Threat Detection
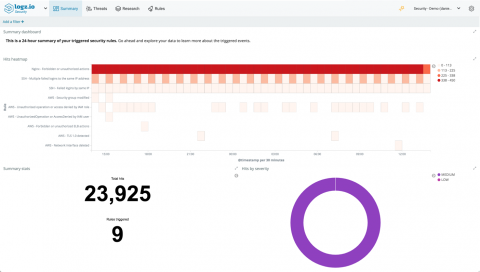
Companies are generating massive amounts of data every minute. It’s impossible, unrealistic, and cost-prohibitive for analysts to spot every threat. That’s why even though breaches are in decline year over year, the first quarter of 2018 saw 686 breaches that exposed 1.4 billion records through hacking, skimming, inadvertent Internet disclosure, phishing, and malware.