Operations | Monitoring | ITSM | DevOps | Cloud
Threat Detection
How does your AWS environment stand up to the MITRE ATT&CK framework?
Best practices for creating custom detection rules with Datadog Cloud SIEM
In Part 1 of this series, we talked about some challenges with building sufficient coverage for detecting security threats. We also discussed how telemetry sources like logs are invaluable for detecting potential threats to your environment because they provide crucial details about who is accessing service resources, why they are accessing them, and whether any changes have been made.
The Strengths of Managed XDR in Real-time Threat Detection and Response
What is Managed Detection and Response (MDR)?
Cybersecurity is a top concern among businesses, especially as the number of cyberattacks, data breaches, and malware infections continue to grow each year. These attacks can happen at any moment during the day, too. It can be a headache trying to keep watch for cyberthreats 24/7 and know how to effectively respond when they are detected, especially for MSPs who have multiple different clients.
How to discover advanced persistent threats in AWS
How Federal Buildings Are Converging Their Cyber And Physical Technologies For Futureproof Security
Improve Response in the Threat Detection Response Equation - Webinar
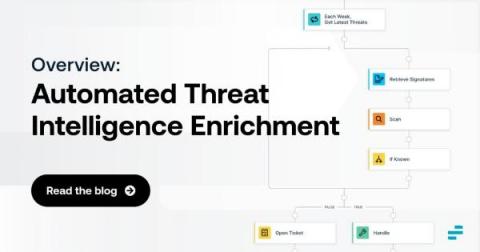
Automated Threat Intelligence Enrichment: An Overview
Discovering security threats is good and well. But, in many cases, simply knowing that a threat may exist is not enough. Instead, you also need threat intelligence enrichment. Threat enrichment plays a critical role in helping to evaluate and contextualize threats, root out false positives and gain the insights necessary to mitigate risks as efficiently and quickly as possible.