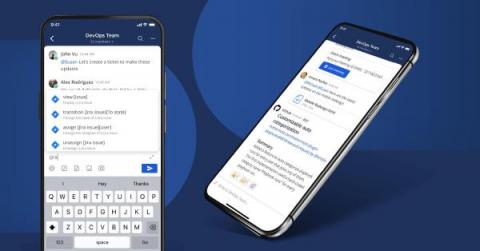
Join the Mattermost mobile beta program: v2.0 is now live!
Get ready for the future of Mattermost mobile. Beta testers can now access Mobile v2.0, including multi-server support — our most requested mobile feature ever. We’re also bringing you a number of usability enhancements and performance improvements to make you productive on the go. If you want to be on the cutting-edge of Mattermost mobile development, we’d encourage you to join the mobile beta program today.