Operations | Monitoring | ITSM | DevOps | Cloud
February 2020
Five worthy reads: XAI, a move from black to white
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. This week, we explore the concept of XAI, Explainable AI.
IT security: Keep calm and monitor PowerShell
In our last release of the PowerShell security series, we talked about how PowerShell could be leveraged by malicious actors to gain unprecedented access to your organization’s critical assets. From enumerating sensitive domain information and carrying out credential-based attacks to running malicious executables in memory (file-less malware), we shined a light on the potential of PowerShell and why it’s an ideal weapon for cyber attackers today.
Windows 10 Migration - Cause and Effects
Leverage analytics to get a unified view of enterprise IT
Is your business PCI DSS compliant?
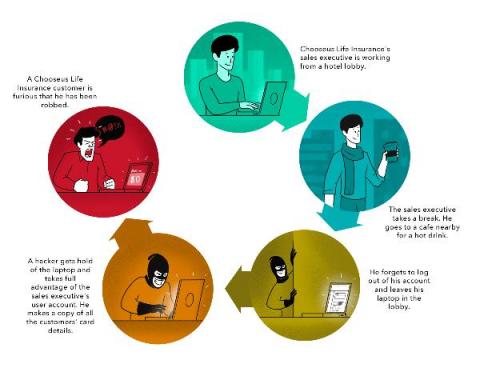
How Chooseus Life Insurance lost its customers’ cardholder details and their trust In August 2019, reporters began flocking to Chooseus Life Insurance’s head office in Detroit after news leaked that thousands of the company’s customers had lost money due to a security breach. The CEO of this life insurance company released the following statement: “We have had your trust for two years.
Resource Management, Images, and more with ServiceDesk Plus 11.1
Five worthy reads: Why AI-as-a-Service, or AIaaS, is quickly growing in popularity
Five worthy reads is a regular column on five noteworthy items we’ve discovered while researching trending and timeless topics. Most companies use some type of “as-a-service” solution to optimize output, and this week, we shed some light on the latest “as-a-service” trend to hit the market, AI-as-a-Service.
Key security functions of unified endpoint management
As part of digital transformation, the adoption of a wide range of devices for work is on the rise. A unified endpoint management (UEM) solution is capable of enforcing management policies and configurations, as well as securing endpoints. In a previous blog, we reviewed the capabilities of a good UEM solution. In this instalment, we look at UEM security features.
Network configuration management: Best practices
Sizing up the CCPA: How the USA's new privacy regulation measures up against the GDPR
The California Consumer Protection (CCPA) act took effect on January 1, 2020, and companies across the globe are scrambling to get their act together to avoid non-compliance penalties. Although enforcement of the CCPA doesn’t officially begin until July 2020, the California Attorney General’s office will still be able to penalize violations that occurred between implementation on January 1 and official enforcement in July.
Recovering from OneDrive for Business ransomware attacks
Ransomware has been a growing threat in recent years, and experts now estimate the cost of these attacks at $7.5 billion in the USA alone in 2019. The affected institutions include 966 government agencies, educational establishments, and healthcare providers. Since most ransomware attacks stem from a small mistake made by one end user, either through phishing emails or stolen credentials, the threat is only expected to increase in the years to come.
Integrating Mobile Device Manager Plus with Jira Service Desk
Windows 7 to Windows 10 - Migration Made Easy!
IT security: Disrupting the cybersecurity kill chain by detecting domain reconnaissance
Cyberattacks are a growing threat, and organizations are investing time and money in security strategies to make certain that their infrastructures are secure. Active Directory (AD) is a constant target for compromise, as it’s at the core of any organization’s security — it handles authentication and authorization for all users in an organization.