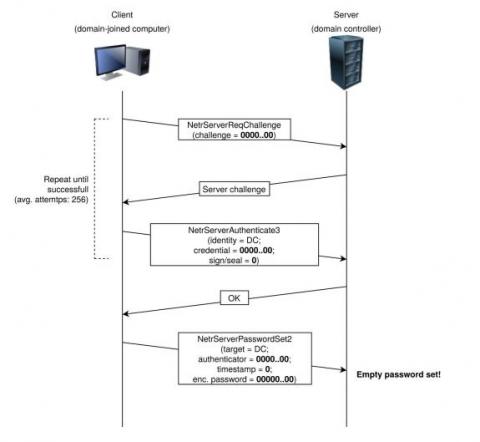
Leverage AI and predictive analysis to cut costs and eliminate downtime
With the promise of unprecedented potential, artificial intelligence (AI) and predictive analytics have permeated into every field of business. Due to their ability to help retail staff serve customers better, personalize video recommendations based on users’ preferences, reduce employee churn, and detect fraud and security threats, AI and predictive analysis are rapidly being adapted across industry verticals.