Operations | Monitoring | ITSM | DevOps | Cloud
Latest Posts
Dependency Redundancy Groups in Icinga 2.14
Icinga 2.14 introduced a new feature that allows to better model complex dependencies between your hosts and services: redundancy groups. Let’s take an e-mail server as an example. In order to deliver outgoing messages, it has to look up the addresses of the destination servers and relies on DNS for doing so. For incoming messages, it has to know which accounts exist and in a corporate environment, this typically means looking up user accounts in a directory service like LDAP.
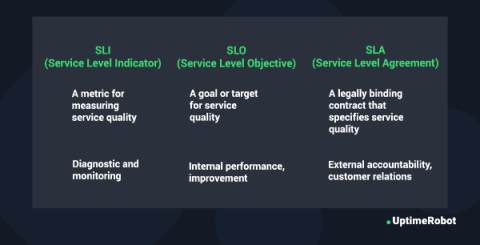
SLA vs. SLO vs. SLI: What's the Difference?
When it comes to managing services effectively, terms like SLA, SLO, and SLI are often thrown around like confetti at a parade. They’re in meetings, in documents, and even in casual office conversations. But if you’re new to the field or simply haven’t had the chance to dig into these acronyms, they can feel like a bewildering alphabet soup. And they can’t be missing on an uptime monitoring blog such as ours! So, what do these terms really mean?
Network Segmentation: Definition and Key Benefits
In the ever-evolving landscape of network security, the challenges faced by Managed Service Providers (MSPs) and technical managers are multifaceted, and the need for robust security measures becomes paramount. Amidst this backdrop, network segmentation remains a pivotal strategy. This article delves into the intricacies of network segmentation, its significance, and a roadmap to its successful implementation.
Greener Cloud Computing with Deep Green and Civo
With more companies switching to cloud service providers, we are seeing a drastic increase in the amount of electricity required to run the data centers that are hosting all the machines required to run these platforms. Currently, data centers produce 3% of global carbon emissions, which is roughly 1.5% of the worldwide electricity demand.
Getting Started with Infrastructure Monitoring
This article was originally published on The New Stack and is reposted here with permission. By taking advantage of monitoring data, companies can ensure their infrastructure is performing optimally while reducing costs. While building new features and launching new products is fun, none of it matters if your software isn’t reliable. One key part of making sure your apps run smoothly is having robust infrastructure monitoring in place.
VMware Was Named an Overall Leader in Cloud Security Posture Management by KuppingerCole Analysts AG
KuppingerCole AG published its report assessing Cloud Security Posture Management (CSPM) solutions in the market for 2023. Their leadership compass helps cloud users find an appropriate solution to meet CSPM needs of an organization to monitor, assess, and manage risks associated with the use of cloud services. Fifteen vendors were assessed based on responses to a questionnaire, strategy briefing, and demo.
A Vicious Cycle: Data Hidden Behind Lock and Key
Understanding production has historically been reserved for software developers and engineers. After all, those folks are the ones building, maintaining, and fixing everything they deliver into production. However, the value of software doesn't stop the moment it makes it to production. Software systems have users, and there are often teams dedicated to their support.
MCU Peripheral Forwarding
PC applications that interact with MCUs are used by developers for a number of reasons, such as data visualization, monitoring during testing campaigns, and command and control via a GUI. In this article, we’ll explore mapping an MCU’s peripherals to your personal computer to simplify development of PC applications built for embedded systems. Like Interrupt? Subscribe to get our latest posts straight to your mailbox.
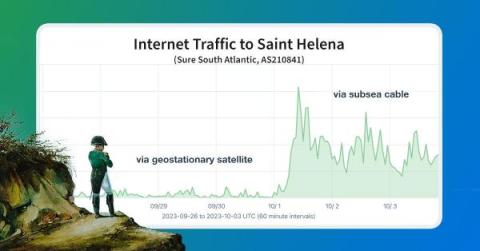
Ending Saint Helena's Exile from the Internet
Just after midnight on October 1, 2023, the remote island of Saint Helena in the South Atlantic began passing internet traffic over its long-awaited, first-ever submarine cable connection. In this blog post, we cover how Kentik’s measurements captured this historic activation, as well as the epic story of the advocacy work it took to make this development possible.