The Anatomy of a Secure Serverless Platform, Pt. 2 -- Development
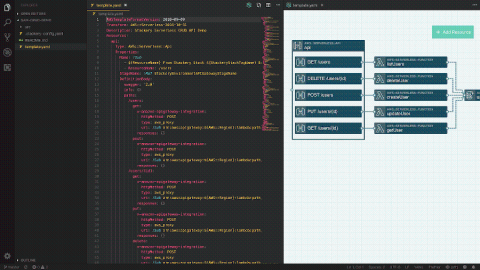
Stackery’s secure serverless platform for AWS offers teams a key resource to help realize the promise of serverless – by automating otherwise complex infrastructure processes, we enable you to leverage the massive suite of AWS tools and services with minimal management overhead. It’s crucial for teams to do this while enforcing security and ensuring adherence to compliance guidelines.