Operations | Monitoring | ITSM | DevOps | Cloud
Latest News
Fundamentals: Application Acceleration and the Benefits for your Service Delivery
Application acceleration is all about improving the responsiveness of a digital service. When clients access web applications, they are expecting near-immediate feedback from servers. Maintaining that level of performance requires ensuring the right resources are available to process requests, shortening the information retrieval process, and maintaining system uptime by warding off threats.
Take Network Monitoring to the Extreme with WhatsUp Gold/Flowmon Duo
Network monitoring is the key to efficient, reliable operation, as well as performance and security. The deeper and more broadly you can monitor (yes, you want to do both), the better your network operates. What if you could combine a superstar in network infrastructure monitoring with the champion of network flow monitoring? You can. Progress, owner of WhatsUp Gold, recently acquired Kemp and their market-leading Flowmon solution.
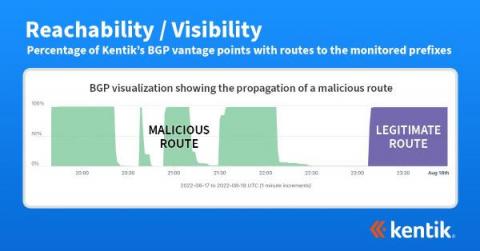
What can be learned from recent BGP hijacks targeting cryptocurrency services
On August 17, 2022, an attacker was able to steal approximately $235,000 in cryptocurrency by employing a BGP hijack against the Celer Bridge, a service which allows users to convert between cryptocurrencies. In this blog post, I discuss this and previous infrastructure attacks against cryptocurrency services. While these episodes revolve around the theft of cryptocurrency, the underlying attacks hold lessons for securing the BGP routing of any organization that conducts business on the internet.
Top 5 Ways MSPs Can Focus on Network Compliance to Boost Revenue
The barriers of entry in the service provider industry have come down-causing the MSP market to grow by nearly 33% last year and reaching nearly $355 billion by 2026.
Paritel Selects Ribbon to Comply with French Government Mandate to Combat Robocalls, Fraud, & Call Spoofing
Harness Continuous Observability to Continuously Predict Deployment Risk
In my previous blog, I discussed how continuous observability can be used to deliver continuous reliability. We also discussed the problem of high change failure rates in most enterprises, and how teams fail to proactively address failure risk before changes go into production. This is because manual assessment of change risk is both labor intensive and time consuming, and often contributes to deployment and release delays.
Make Your MSP a Recession-Proof Business
The Cloud And SD-WAN
Ransomware: Latest Variants and Trends on the Rise
Here in this blog, we will talk about some of the emerging ransomware you should know about and how you can prevent such attacks.