What is SSE vs SASE, and is SASE Dead?
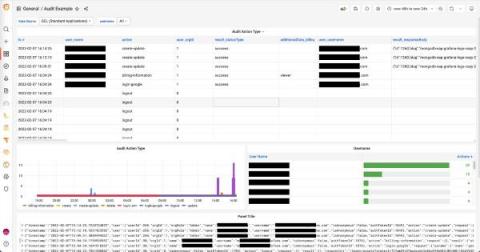
Gartner introduced a new security architecture called Security Service Edge, or SSE, back in March 2021. Now finally, after a long wait, they’ve just published their first Magic Quadrant for SSE in February 2022. This begs the question, is SASE dead? To answer, we need to look at what is SSE vs SASE, and what are the challenges SSE addresses. For easy reference, Gartner created the following SSE definition.