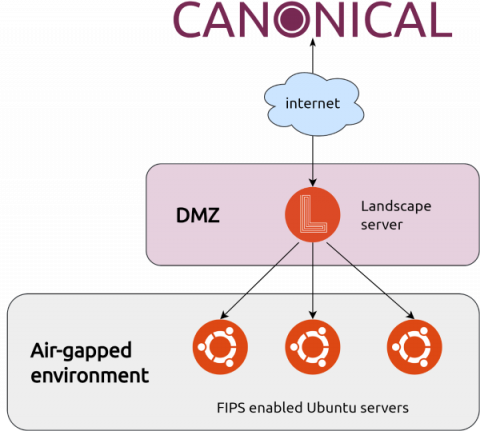
Five Key Steps for Database Security in the Cloud Age
As business has become more digital, data has become the most valuable asset of many organizations. But protecting that data has also become much more complicated as organizations increasingly migrate it to a mix of public and private cloud infrastructures, such as Microsoft Azure, Amazon Web Services, and Google Cloud.