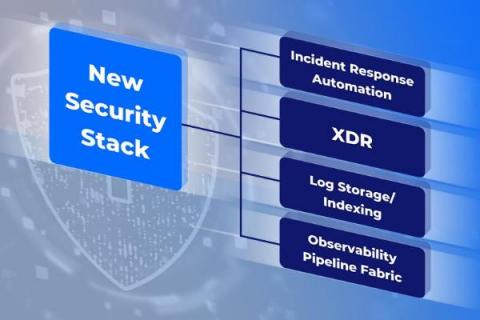
SOAR Security: 7 Disadvantages of SOAR Solutions
We’ve said it before, and we’ll say it again: Security Orchestration, Automation and Response (SOAR) platforms are great tools for helping teams work smarter, faster, and more efficiently against security risks. But, used on their own, SOARs are far from perfect for meeting the full security needs of the modern organization.