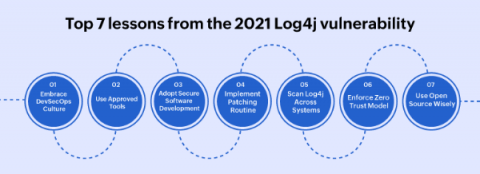
Puppet Enterprise installation and self-signed Intermediate CA
This article is about how to install Puppet Enterprise using your own self-signed Intermediate CA (Certificate Authority). In some environments, regulations require you to intercept and inspect all SSL traffic to detect malicious activities that could otherwise masquerade as legitimate encrypted traffic. This requires the ability to decrypt and re-encrypt the stream in real time, which can only be done with the proper certificates installed.