Cyber-hygiene 101 during remote working: Protecting your digital identities with multi-factor authentication
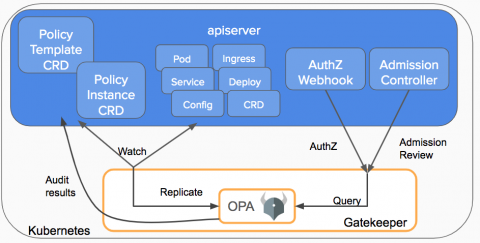
When organizations shift to a work-from-home environment, identity and access management (IAM) takes center stage. Organizations with remote workforces must fortify their IAM policies and tools for a better user experience to ensure productivity, while also handling all the security challenges remote work presents to ensure data and system security. One of the biggest risks an organization faces when its workforce goes remote is unnecessary and unauthorized access to organizational data.