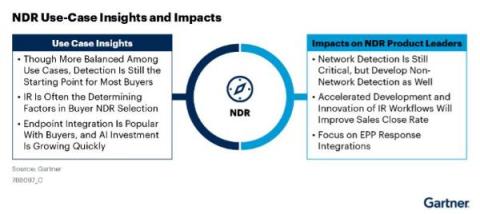
Gartner Lays out Three Use Cases of Network Detection and Response (NDR) Adoption
The Gartner recent report, “Emerging Tech: Top Use Cases for Network Detection and Response”, lays out three primary use case drives, which include: Before we dive deeper into Gartner findings, let’s talk about NDR from a high level.